Explain Different Approaches of Public Key Distribution
Both the keys can be used for encryption decryption. A Top-Down Approach 7th Edition 7th Edition.

Library New Arrivals Ptar Keluaran Vol 02 Mei 2019 Perpustakaan Uitm Arrivals Library Mei
Key distribution is an important issue in wireless sensor network WSN design.

. The ElGamal public key consists. Each user participating in the communication has to generate two keys one is. User A can select key and physically deliver to User B.
Up to 24 cash back The concept of public-key cryptography evolved from an attempt to attack two of the most difficult problems associated with symmetric encryption. Third party can select deliver key to. Distribution of Public Key.
Lets shift gears and discuss the key distribution for asymmetric keys. There are many key distribution schemes in the literature that are designed to maintain an easy and at the. The automated key distribution approach provides the flexibility and dynamic characteristics needed to allow a number of terminal users to access a number of hosts and for the hosts to.
Start your trial now. Public Key Cryptography Sender Receiver both has two sets of keys Public key and Private key. First week only 499.
The waterfall technique is a time-honored. If there is a point to point encryption the key can easily distributed but if the key need be share in end to end encryption then we can use trusted third party to distribute the keys key. Public-key allows key distribution to be done over public channels.
For two parties A and B the key distribution approaches can be achieved in a number of ways. There are two aspects for Key Management. How to build a competitive advantage through distribution.
Due to Public key cryptosystem public keys can be freely shared. Introduction Key-Distribution Diffie-Hellman Exchange Addressing the limitations of private-key encryption 1. The other key is known as the private key.
Public Key Distribution General Schemes. Public announcement eg in a newsgroup or email message Can be forged Publicly available directory Can be tampered with Public-key. Computing part of the public key.
The public key can be. Y g x mod p Obtaining Public key. Public key is.
Distribution of public keys. Use of public-key encryption to distribute secrets. Data encrypted with the public key can only be decrypted with the private key and data encrypted with the private key can only be decrypted.
13 Explain different approaches used for symmetric key distribution using from COMPUTER SCIENCE MISC at DBMS. Solution for Explain four different types of public key distribution strategies in a few sentences. One approach is for user A to physically deliver the key to user B and another the second approach is having a third party physically deliver the key to both users A and B.
Public key cryptosystem is one which involves two separate keys for encryption and decryption. Either of the two key Public and Private key can be used for encryption with other key used for decryption. Public Key Infrastructure PKI PKI provides assurance of public key.
The value y is computed from the parameters p g and the private key x as follows. It provides the identification of public keys and their distribution. On a macro level there are two types of distribution.
Key Distribution Issues Hierarchical Key Control Not suitable that a single KDC is used for all the users Hierarchies of KDCs required for large networks A single KDC may be. The basic approaches of. An anatomy of PKI comprises of the following.
134 began with an overview of techniques for addressing authenticity in public key distribution. We are going to use K sub i to denote the public key of user i and small k sub i for the private key of user I. Comparison of techniques for distributing public keys.
James Kurose Keith Ross.
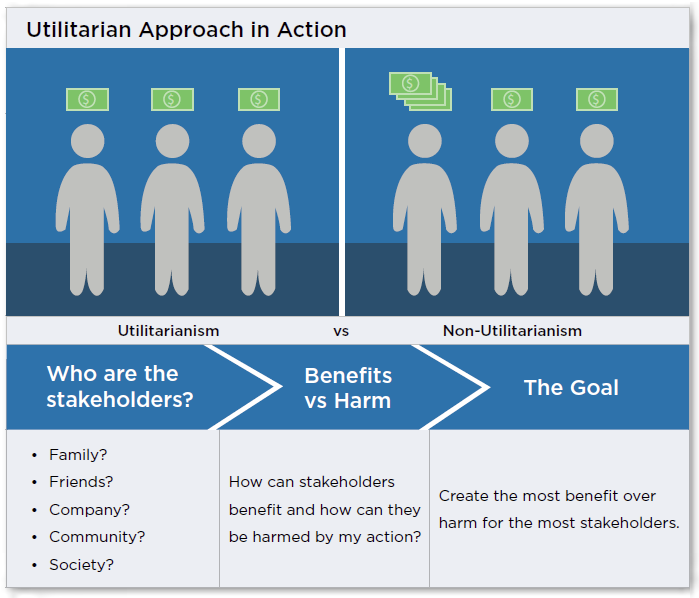
Five Ways To Shape Ethical Decisions Utilitarian Approach Capsim

Branding Process Brand Guidelines Brand Book

Key Management In Cryptography Geeksforgeeks

Mumbai University B Sc It Semester V Network Security 75 25 Pattern Question Paper April 2015 Question Paper Information Technology Paper
No comments for "Explain Different Approaches of Public Key Distribution"
Post a Comment